Understanding the Attack Chain Helps to Counter Threats
Summary
Security teams are struggling to keep pace with the changes in their networks. Hybrid work, multi-cloud, the explosion of IoT and BYOD devices, and 5G. Meanwhile, cybercriminals have been undergoing their digital transformation. Machine learning and agile development, new sophisticated attacks, combined with Dark Web crime-as-a-service offerings mean that attacks are faster, harder to detect, and …
Continue reading “Understanding the Attack Chain Helps to Counter Threats”
Security teams are struggling to keep pace with the changes in their networks. Hybrid work, multi-cloud, the explosion of IoT and BYOD devices, and 5G. Meanwhile, cybercriminals have been undergoing their digital transformation. Machine learning and agile development, new sophisticated attacks, combined with Dark Web crime-as-a-service offerings mean that attacks are faster, harder to detect, and better at finding and exploiting vulnerabilities. A recent FortiGuard Labs threat report demonstrated that ransomware increased tenfold in the last year. Threat trends over the year continued to evolve and it is not slowing down.
Understanding the MITRE Attack Chain
Effectively defending against cyberattacks today requires security teams to work smarter rather than harder. Cybercriminal strategies target every link in an attack chain, from gathering information and gaining access, to moving laterally across the network to discover resources to target, to evading detection while exfiltrating data. Traditional security strategies, however, tend to only focus on a handful of attack components, which gives criminals a significant advantage.
To address today’s challenges, security teams need a combination of tools, strategy, automation, and skilled professionals to monitor the entire attack chain and automate as much of the process as possible so that human resources can be focused on higher order analysis and response. Choosing such tools, however, requires understanding the entire length of the attack chain and how vulnerabilities in each of its links can compromise the security of your network.
To assist with this, MITRE has mapped the attack chain into fourteen discrete links, along with examples of the types of attacks that target each link in that chain. To effectively counter today’s advanced threats, security teams need to familiarize themselves with each link in the chain and map them directly to functional areas and tools within their networks.
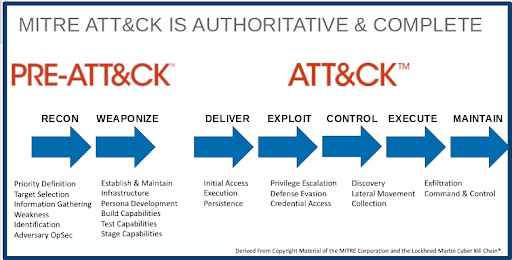
Understanding and Implementing The Fourteen Discrete “Links”
-
- Reconnaissance: This is the adversary’s planning phase for future attacks. The activities focus on information gathering which could be performed actively or passively depending on the requirement. Specifically, the actor is looking to learn more about the organization including its infrastructure and employees. The more information the adversary knows about the target the better chance of a successful attack.
- Resource Development: Before an attacker can start their cyber mission, they need to make sure they have the right resources to execute the mission. The attacker will need to determine whether they will create, purchase, steal or compromise the right resources to support the mission. Examples could be things like domains, web services, VPNs, infrastructure, accounts/emails, malware, and exploits.
- Initial Access: Exploiting known vulnerabilities in servers, compromising websites or applications, or taking advantage of successful spearphishing attacks allow attackers to wedge a foothold into the edge of the network.
- Execution: This is the point where an attacker executes a binary, command, or script to begin their network reconnaissance and exploitation process.
- Persistence: Once an attacker has established a foothold, the next goal is to avoid detection. Creating or manipulating accounts, applying rootkits, using run keys, or exploiting tools like application shimming enable attackers to persist in place while they explore the network for potential targets.
- Privilege Escalation: Basic access does not allow an attacker much opportunity to explore the network. To move around the network and access resources worth stealing, an attacker needs higher network privileges.
- Defense Evasion: To move through a network undetected, especially when exfiltrating data, attacks need to avoid detection by things like behavioral analytics and IPS tools. Techniques such as clearing files, learning and mimicking normal traffic behaviors, or disabling security tools are just a few of the full range of tools available to today’s hackers.
- Credential Access: In many organizations, critical data and other resources are protected behind a wall of security that require appropriate credentials for access. Unfortunately, gaining access to credentials isn’t always that difficult. They are stored in files or in a registry that attackers can exploit, techniques like hooking allow cybercriminals to intercept traffic to uncover credentials, and account manipulation can involve things like adding or modifying the permissions to the account being used to access the network.
- Discovery: Not all data exists in the segment of the network that was broken into. Many of the same techniques used to this point are used again to determine where valuable resources exist.
- Lateral Movement: and to Then, allow an attacker to can move laterally between network segments, whether they are local to the breach or at some remote physical or virtual data center.
- Collection: Once an attacker has identified a payload, they need to collect that data needs and extract it from the network without being detected. This is often the trickiest part of the process, as this may involve massive amounts of data.
- Exfiltration: But if Once a cybercriminal has carefully crafted each attack element to this point, they are often able to remain inside a compromised network for months, slowly moving data to other resources that are under less scrutiny, and eventually out of the network.
- Command and Control: The final step is for attackers to cover their tracks completely. Multi-hop proxies, data obfuscation, and multi-stage exfiltration are just a few of the techniques cybercriminals use to ensure that stolen data cannot be tracked and traced back to them.
Work Smarter by Utilizing the MITRE Attack Chain
Addressing the entire attack chain needs to be combined with understanding how the network functions, including the impact that future business requirements will have on the network. Mapping those functions to the attack chain allows security teams to think comprehensively about security threats.
Breaking security down into the fourteen MITRE attack chain links has two goals.
- The first is to engineer as much risk out of the network as possible by addressing weaknesses inherent in each link of the attack chain before an attack occurs. This may include hardening protocols to prevent their exploitation, turning off unused ports, and baselining all known traffic so that new applications or escalating privileges can be identified. Each of these activities can be mapped to multiple attack chain links. So can behavioral analytics, which can identify when a device begins behaving strangely, such as FTPing data out of the network. Even activities such as patching or replacing vulnerable devices, and subscribing to threat intelligence feeds so you are tuned to current attack methodologies and malware can be mapped to multiple links in the attack chain.
- The second goal is to apply security strategically so that fewer security tools can address more challenges. This allows you to keep the number of management and orchestration consoles you need to monitor under control. It also enhances your ability to implement AI and machine learning such as Endpoint detection and Response technologies to address challenges at digital speeds. Tools like Network Access Control and zero trust network access ensure that you are aware of every device on your network, while SIEM devices ensure that threat intelligence is dynamically collected and correlated from every devices deployed in every corner of your network. Keep in mind that once you have chosen the right technologies and have the proper configurations and logging its equally as important to you have the right people and processes in place to ensure the return on investment with those technologies. Remember a strong cyber defense is comprised of People, Processes and Technologies.
At the same time, consistency in security policy implementation and enforcement across different network ecosystems is critical. For example, you should deploy the same NGFW solution in every part of your network, whether physical or virtual. This ensures that security protocols and enforcement are applied consistently and that you can monitor and manage your systems through a single central console.
Approaching Security Strategically
Of course, this strategic approach may require radically rethinking your security deployment. Tools have to be fully integrated so that the network can identify and address security threats as a unified system. A self-healing network requires security devices to share and correlate threat intelligence to identify and monitor every device, track applications, detect malware, isolate infected devices, and coordinate responses across a wide variety of network ecosystems, —from multi-cloud infrastructures, platforms, and applications, to remote workers and IoT devices, to next-gen branch offices connected to the cloud and physical resources through Secure SD-WAN. Threat intelligence and response also needs to be driven into each link in the MITRE attack chain. And where possible, AI and machine learning need to be applied so that your integrated security fabric can respond to threats at digital speeds and human resources can provide critical supervision.
The MITRE Attack Chain to Shift Proactive Thinking
A breach resulting in the loss of data can occur in minutes or hours. And yet, it can take weeks or months for most security breaches to be detected. By that time, the perpetrators and your data are long gone. The only way to get out in front of this challenge is to change from a traditional tactical approach that relies on isolated legacy security tools to an integrated strategy that enables you to see and control your entire networked environment, link by link, to identify anomalous behavior and automatically thwart attackers before they have managed to escalate themselves up the attack chain.
This is a partnered post.

Elon Musk forms several ‘X Holdings’ companies to fund potential Twitter buyout
3 Mins Read
Thursday’s filing dispelled some doubts, though Musk still has work to do. He and his advisers will spend the coming days vetting potential investors for the equity portion of his offer, according to people familiar with the matter









 Listen to the Article
Listen to the Article  Daily Newsletter
Daily Newsletter